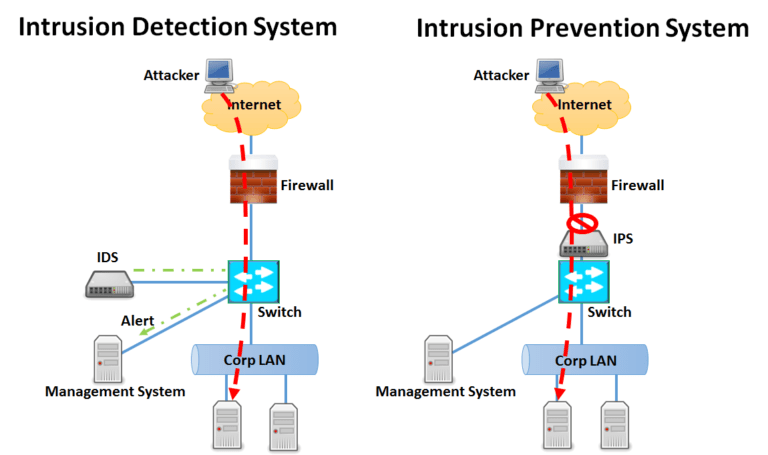
IDS-IPS
An Intrusion Detection Sensor (IDS) is a tool that most obviously detects things; Snort or Suricata or ET include a large array of ‘signatures’ and or methods for detection. For each network this answer will vary, though generally it is looking for unusual traffic. In the simplest terms, it’s traffic you don’t want on your network, whether that is policy/misuse (IM, Games, etc..) or the latest malware.
The segment of your network the IDS will monitor. Monitoring traffic at the ingress/egress point will show you what comes and goes (after the firewall policy approves of course)
Monitoring all of the traffic via Wan to internal switch, like your LAN or a DMZ, will allow the IDS to monitor user activity or key servers, but it won’t see things happening on other parts of the network. Unless you have unlimited resources, you may not be able to monitor everything on the network, so a key decision will be which traffic matters the most and which segment provides the best vantage point 'automatically'
IDS can passively monitor more than one segment and can monitor traffic that an IPS or UTM would never see, such as the traffic staying entirely within a LAN or DMZ. An IDS, therefore, could alert on a desktop machine attacking other desktop machines on the LAN, something the IPS or UTM would miss due to being inline.
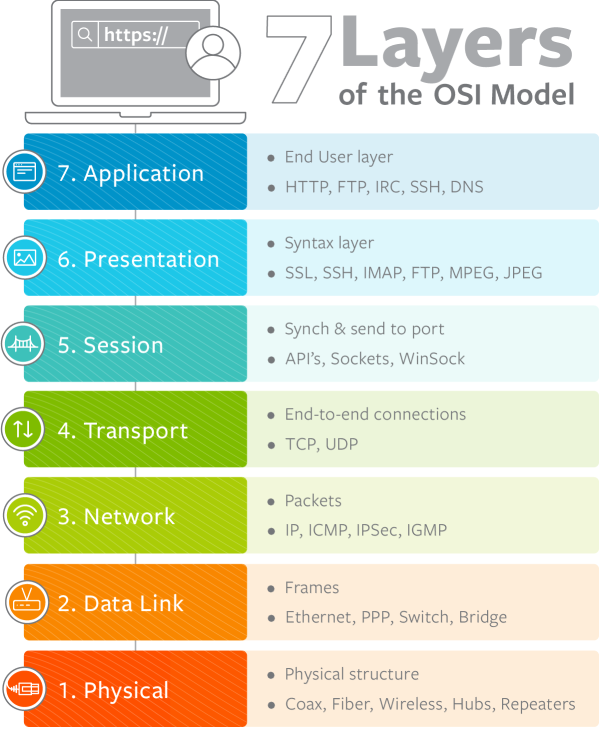
Simply said Traditional Firewall can only "allow or block" OSI layers 2 to 4 traffic
But IPS/IDS can detect and defense OSI layers 5 to 7 traffic.
Unfortunately, most network threats are happening on OSI layer 5 to 7 ...
IPS and IDS
An IPS (Intrusion Prevention Sensor) is an IDS in most regards, save for the fact it can take action inline on current traffic. It is amazing, by their nature, must be inline and therefore can only see traffic entering and leaving an area. A huge concern is that an IPS can prevent business legitimate or revenue-generating traffic from occurring (an IPS, remember, can alter traffic flow). IPS actions include drop, reset, shun or custom scripted actions and all of this occurs immediately upon signature match. This potentially negative action makes the person responsible for security now responsible for loss in revenue should the IPS drop legitimate traffic. In our experience, IPS devices make great tools as long as you also leverage the key components that differentiate the IPS.
Make sure your IPS devices is capable of “failing open”; this means if any part of the application fails or even the chassis fails (power loss anyone) the unit continues to pass traffic. No one wants a brick impeding the flow of data.
Also realize that only a small portion of the signatures that fire should actually be allowed to take action on traffic. To help reduce false positive rates one should have very well defined home net or protected ranges allowing direction oriented signatures to be more effective. You will also need to spend quite a bit of time reviewing alarm and event output to ensure the signatures allowed to take action are working as intended. You can expect to spend more time up front and more time at each signature update looking at which signatures the vendor has chosen to take action and considering how that can impact your traffic. We have seen this work best in settings where firewalls are not very favorably looked upon between “open” network segments.
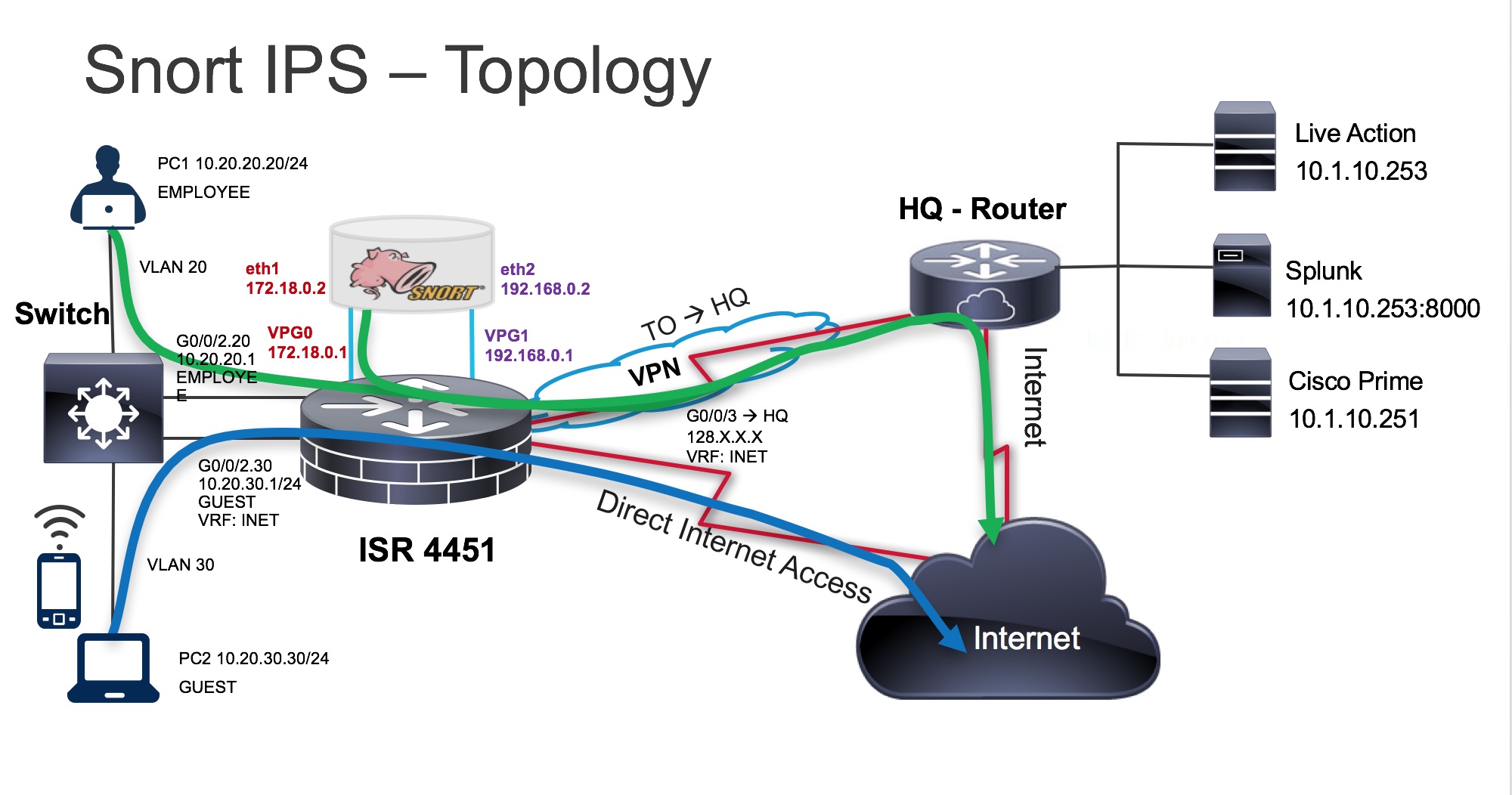
Snort is a Network intrusion prevention system (IPS), capable of performing real-time traffic analysis and packet logging on IP networks. It can perform protocol analysis, content searching/matching, and can be used to detect a variety of attacks and probes, such as buffer overflows, stealth port scans, CGI attacks, SMB probes, OS fingerprinting attempts, and much more.
Suricata is a mature, fast and robust network threat detection engine.
The Suricata engine is capable of real time intrusion detection (IDS), inline intrusion prevention (IPS), network security monitoring (NSM) and offline pcap processing. detection of complex threats. Suricata’s fast paced community driven development focuses on security, usability and efficiency.
The Suricata project and code is owned and supported by the Open Information Security Foundation (OISF), a non-profit foundation committed to ensuring Suricata’s development and sustained success as an open source project.