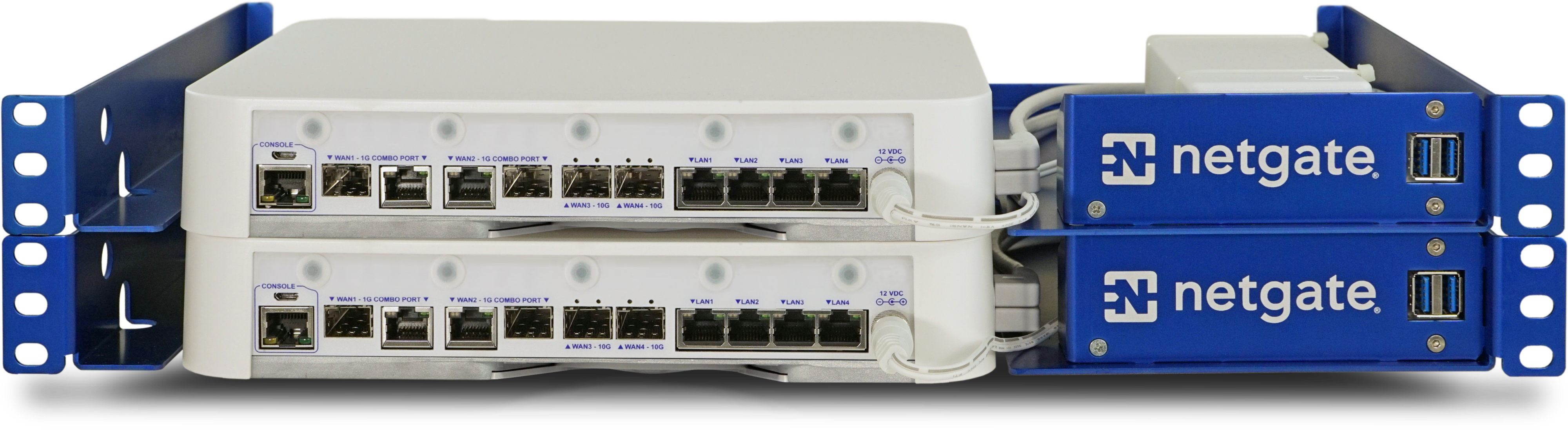
High Availability
This document covers configuration of a High Availability cluster using the following features:
- CARP for IP address redundancy
- XMLRPC for configuration synchronization
- pfsync for state table synchronization
With this configuration, two units act as an “active/passive” cluster with the primary node working as the master unit and the secondary node in a backup role, taking over as needed if the primary node fails.