Do you have an outdated firmware Watchguard ... ?
Are you tired of the expensive yearly subscription ... ?
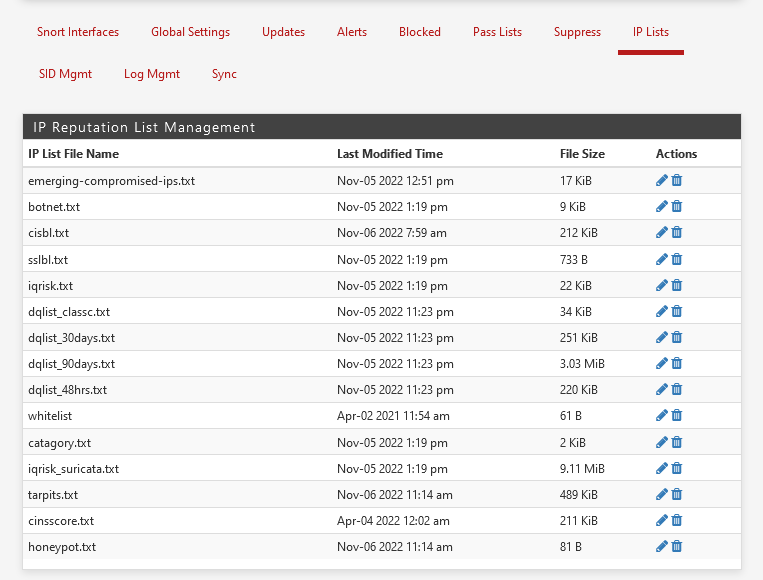
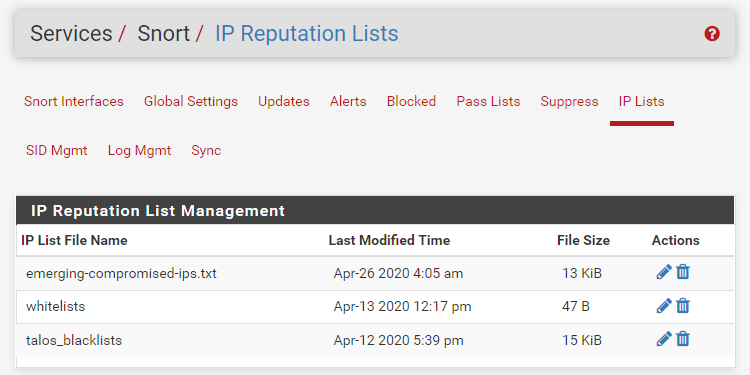
Do you like to have the Free live update of IDS, IPS, IP reputation, ET, Cisco autosense, autodefense ...
You can consider upgrade to pfsense ... all firewall rules can be kept & remain unchanged
We are offering a 'unharmful' upgrade by using a new pfsense M.2 SSD or a new pfsense sata SSD, it is a reborn of your outdated Watchguard firewall. (you original Watchguard firmware will be kept in the same hardware)
|
Watchguard XTM 505 Watchguard XTM 510 Watchguard XTM 520 Watchguard XTM 530 |
 |
call +852.23120878 for support |
WatchGuard XTM 5XX Series Firewall Appliance with latest version pfsense and come with free Cisco autosense, autodefense subscription.
What a magical cost effective combination ... ?
WatchGuard Model comparision :
| WatchGuard Model | XTM 505 | XTM 510 | XTM 520 | XTM 530 |
|---|---|---|---|---|
| Ideal For | Main offices that need performance-driven security that's priced right | Main offices / headquarters that want security with fast throughput and room to grow | Main offices / headquarters looking for enterprise-grade performance and security in an all-in-one solution | Main offices / headquarters that require enterprise-grade performance and powerful security with flexible, centralized management |
| Hardware | ||||
| Model Upgradeable | N/A | |||
| Interfaces | 6: 10/100/1000 and 1:10/100 | 6: 10/100/1000 and 1:10/100 | 6: 10/100/1000 and 1:10/100 | 6: 10/100/1000 and 1:10/100 |
| Security | ||||
| Application Proxies | HTTP, HTTPS, SMTP, FTP, DNS, TCP, POP3, SIP, H.323, TFTP | |||
| Intrusion Prevention (DOS, DDOS, PAD, port scanning, spoofing attacks, address space probes, and more) | ||||
| Wireless Models Only | N/A | N/A | N/A | N/A |
| User Authentication with transparent Windows authentication | ||||
| Performance | ||||
| Firewall Throughput** | 1.5 Gbps | 1.8 Gbps | 2.2 Gbps | 2.6 Gbps |
| VPN Throughput** | 210 Mbps | 350 Mbps | 550 Mbps | 750 Mbps |
| AV Throughput** | 520 Mbps | 625 Mbps | 760 Mbps | 900 Mbps |
| IPS Throughput** | 500 Mbps | 600 Mbps | 735 Mbps | 870 Mbps |
| XTM Throughput** | 330 Mbps | 395 Mbps | 480 Mbps | 570 Mbps |
| Concurrent Sessions* (bi-directional) |
40,000 | 50,000 | 100,000 | 350,000 |
| VPN Tunnels | ||||
| Branch Office VPN Tunnels (Max.) | 65 | 75 | 200 | 600 |
| Mobile VPN with SSL (Incl/Max) | 1 / 65 | 1 / 75 | 1 / 300 | 1 / 600 |
| Mobile VPN with IPSec Client Licenses (Bundled) | 5 | 25 | 50 | 400 |
| Mobile VPN with IPSec Tunnels (Max.) | 75 | 100 | 300 | 1,000 |
| VPN Authentication | ||||
| Management | ||||
| Optional Centralized (Multibox) Management. Optional licenses enable Drag and Drop VPN and one-touch appliance updates. | 4-device WatchGuard System Manager license included with purchase. or can upgrade to Free pfsense, Free VPN, Free HAproxy, Free High Available Sync (pfsync) ... |
|||
| Networking Features | ||||
| Dynamic NAT | ||||
| Static NAT | ||||
| One to One NAT | ||||
| VLAN | 75 | 75 | 75 | 75 |
| Policy-Based Routing | Optional with Fireware XTM Pro but free in pfsense | Optional with Fireware XTM Pro but free in pfsense | Optional with Fireware XTM Pro but free in pfsense | Optional with Fireware XTM Pro but free in pfsense |
| WAN Failover | ||||
| Multi-WAN Load Balancing | Optional with Fireware XTM Pro but free in pfsense | Optional with Fireware XTM Pro but free in pfsense | Optional with Fireware XTM Pro but free in pfsense | Optional with Fireware XTM Pro but free in pfsense |
| Server Load Balancing | Optional with Fireware XTM Pro but free in pfsense | Optional with Fireware XTM Pro but free in pfsense | Optional with Fireware XTM Pro but free in pfsense | Optional with Fireware XTM Pro but free in pfsense |
| Traffic Management/QoS | ||||
| High Availability Active/Active or Active/Passive | Optional with Fireware XTM Pro but free in pfsense | Optional with Fireware XTM Pro but free in pfsense | Optional with Fireware XTM Pro but free in pfsense | Optional with Fireware XTM Pro but free in pfsense |
| Dynamic Routing | Optional with Fireware XTM Pro but free in pfsense | Optional with Fireware XTM Pro but free in pfsense | Optional with Fireware XTM Pro but free in pfsense | Optional with Fireware XTM Pro but free in pfsense |
| VoIP (SIP and H.323)Support | ||||
| Networking Features | ||||
| Application Control | Included with Security Bundle but free in pfsense AppID | Optional but free in pfsense AppID | Optional but free in pfsense AppID | Optional but free in pfsense AppID |
| Reputation Enabled Defense | Included with Security Bundle but free in pfsense | Optional but free in pfsense | Optional but free in pfsense | Optional but free in pfsense |
| spamBlocker with Virus Outbreak Detection | Included with Security Bundle but pfBlockerNG is free in pfsense | Optional but pfBlockerNG is free in pfsense | Optional but pfBlockerNG is free in pfsense | Optional but pfBlockerNG is free in pfsense |
| Gateway AntiVirus/ Intrusion Prevention Service (IPS) | Included with Security Bundle but free in pfsense | Optional but free in pfsense | Optional but free in pfsense | Optional but free in pfsense |
| WebBlocker with HTTPS URL filtering | Included with Security Bundle but free in pfsense | Optional but free in pfsense | Optional but free in pfsense | Optional but free in pfsense |
| LiveSecurity® Service | 1-year and 3-year subscriptions available, but free in pfsense | |||
*Concurrent sessions here represent the number of bi-directional connections.
**Throughput rates will vary based on environment & configuration.














.png)